Forefront TMG 2010 has been built on
top of the core capabilities delivered in Microsoft Internet Security
and Acceleration (ISA) Server 2004/2006 in order to deliver a
comprehensive, enhanced and integrated network security gateway.
Forefront TMG provide additional protection capabilities to help secure
the corporate network from external/Internet-based threats. Forefront
TMG 2010 prevent abuse of networks from internal and external entity.
Forefront provide more management capabilities in terms security and
protection. Forefront TMG 2010 is available in Standard Edition and
Enterprise Edition. Standard version does not support Array/NLB/CARP
support and Enterprise Management. For E-mail Protection both version
requires Exchange license.
Forefront TMG 2010 provide the following enhanced protection capabilities:
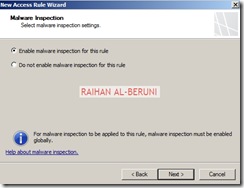
Malware inspection
URL filtering
HTTP filtering
HTTPS inspection
E-mail protection
Network Inspection Systems (NIS)
Intrusion detection and prevention
Secure routing and VPN
Processor- Intel Xeon (Dual core/Quad-core/i7) or AMD Opteron (dual core/quad core). Intel Hyper-Threading Technology enabled in bios if Intel server board.
RAM-8GB
Disk Space –50GB systems partitions and 150GB logging +60GB-100GB Web caching in a separate partition. RAID 5 config would be highly recommended.
NIC- 2 Gigabit NIC with redundant config (number of NICs depends on deployment scenario)
Important! Forefront TMG has been built on 64 architecture.
Microsoft .NET Framework 3.5 SP1
Windows Web Services API
Network Policy Server.
Routing and Remote Access Services.
Active Directory Lightweight Directory Services Tools.
Network Load Balancing Tools.
Windows Power Shell
Windows Installer 4.5
Important! It’s not recommended to install any application or programme in TMG server other then antivirus program. It must be a dedicated server for Forefront TMG. Disable unnecessary services after installing operating systems. Install Machine Certificate from Enterprise Root CA Authority before installing TMG. TMG server must be a member of Active Directory Domain.
Click continue on UAC authorization prompt.
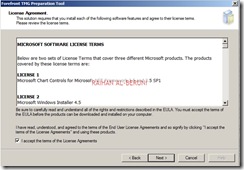
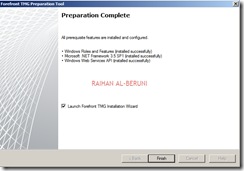
Check Launch TMG installation. Click finish.

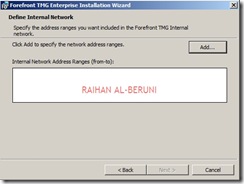
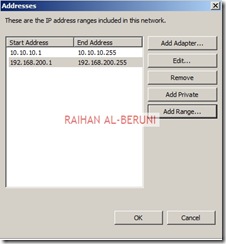
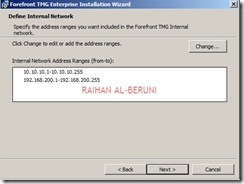
Add ranges of internal IP address For example: 10.10.10.1 to 10.10.10.255. You can as many subnet ranges as you have for internal networks.



Open Forefront TMG Management from start menu. TMG will automatically prompt you for initial configuration.
Step1: Network Setup Wizard—Use to configure network adapters on the server. Network adapters are associated with a unique Forefront TMG network. Note that you must have static IP address in all NIC of TMG server before you proceed for network settings.

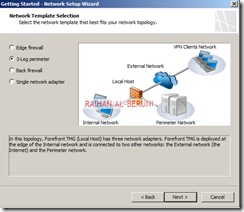
This is highly important part of config because in this section you will mention what type of network topology you are going to use. Here, I am configuring De-militarized Zone (DMZ) or 3-Leg Perimeter. You have to select your desired config.

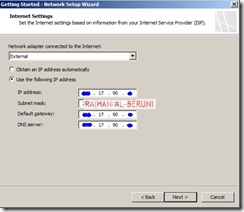

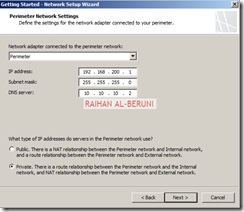
In this section, you have to select the behaviour of the traffic among internal, perimeter (DMZ) and external network. For example, My Forefront TMG 2010 server has been configured to route between internal and perimeter and NAT in between perimeter and external as I choose private networks in perimeter. So that I can hide IP addresses of my perimeter networks.
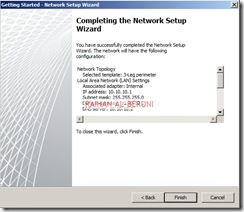
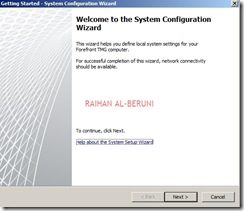
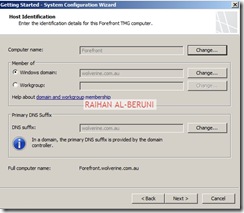
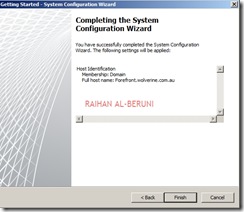
Step2: System Configuration Wizard—Use to configure operating system settings, such as computer name information and domain or workgroup settings
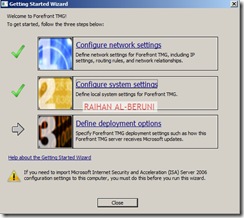
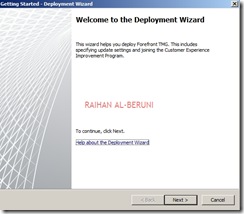
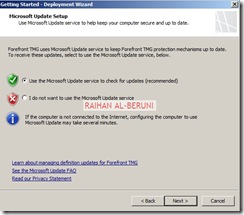
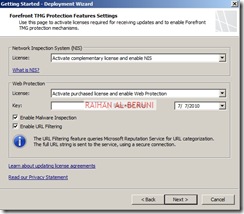
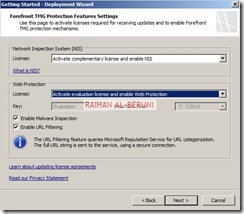
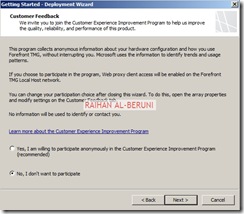
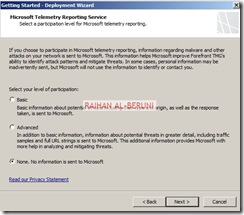
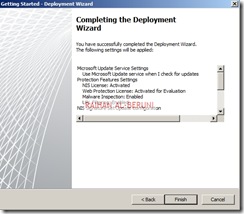
Step3: Deployment Wizard—Use to configure malware protection for Web traffic, and to join the customer feedback program and telemetry service.

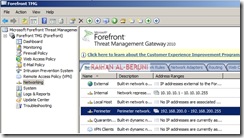
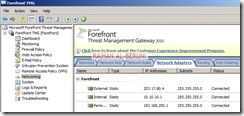
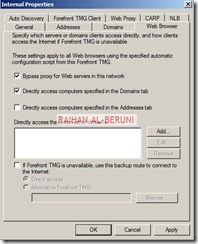
Select networking>Select Networks Tab>Double click on Internal. You will be presented with Internal Properties. Configure all the tabs as shown below.
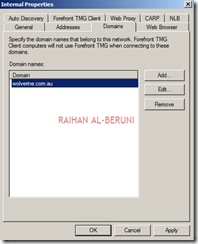
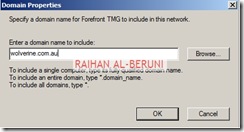
In the domain tab, add internal domain(s). For example: *.wolverine.com.au
In the web browser tab, check Bypass Proxy… and Directly Access….
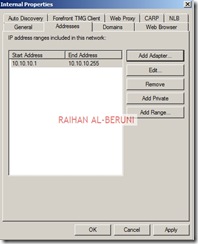
Verify all your internal IP addresses you added during installation. In this window you can add more internal IP addresses if you want.
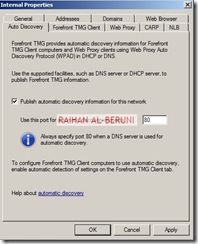
Check Publish Automatic Discovery information for the network and use port 80 as default.
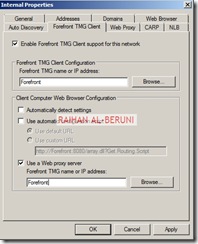
In Forefront TMG Client settings, Check Enable Forefront TMG client support for this network. un-check Automatically detect settings and Use automatic scripts.., Check Use a Web proxy server
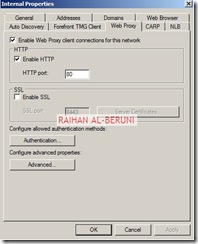
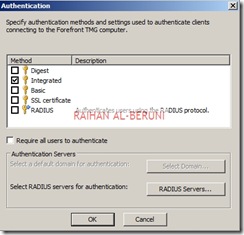
In the Web Proxy Tab, Enable HTTP and use port 80 as default. However, you can use port 8080 if you want. Click on authentication and check integrated. Click on advanced and check unlimited. Now Apply and ok.
Apply changes.
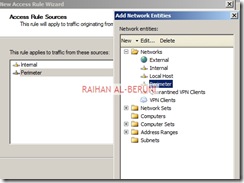
Now repeat all these config for perimeter networks as you did for internal networks.
Connecting Active Directory, DNS and DHCP
Setup connectivity with Microsoft Active Directory, DNS and DHCP. Click on monitoring>click connectivity verifiers>Click Create New Connectivity Verifier. Create connectivity for Active Directory, DNS and DHCP.
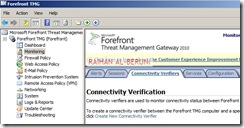
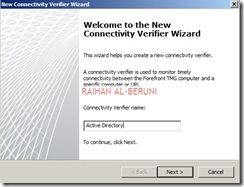
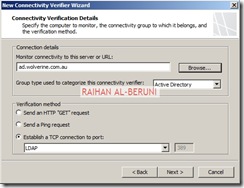
Click Next and Finish. Repeat it for DNS and DHCP. If you have a upstream Proxy, connect to upstream proxy using similar method.
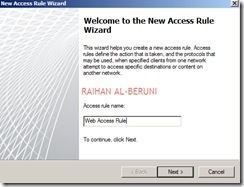
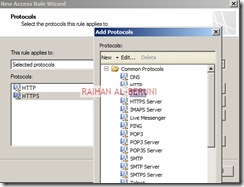
Create HTTP and HTTPS rule
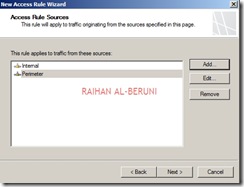
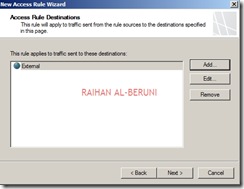
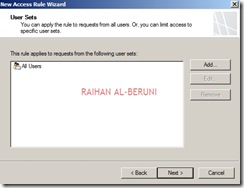
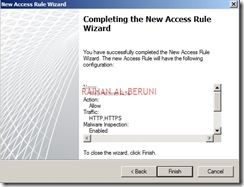
By default all access rules are denied. Now Create web access rules for internal networks allowing HTTP and HTTPs traffic pass through from internal network to external and perimeter. Also allow HTTP and HTTPs traffic pass through from perimeter to external and internal. Click Firewall Policy>Click Create Access Rule on Task Pan.
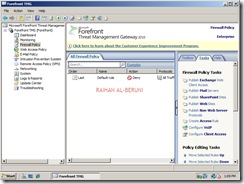

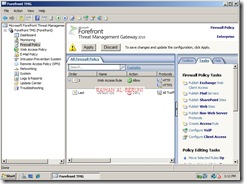
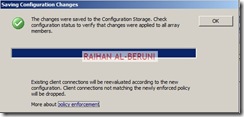
Test Forefront TMG Setup
Now moment of truth. Log on to a computer using domain user credential in any internal network. Setup proxy in IE connections and browse internet.
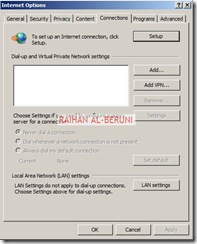
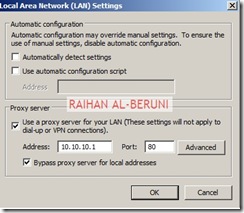
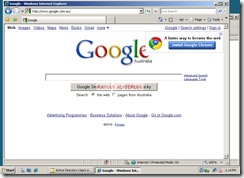
 Thumps UP.
Thumps UP.
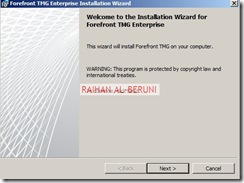
Insert the Forefront TMG DVD into the DVD drive, or run autorun.hta from the shared network drive.
On the main setup page, click Run Installation Wizard.
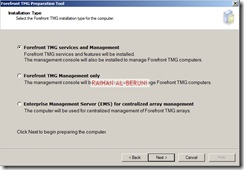
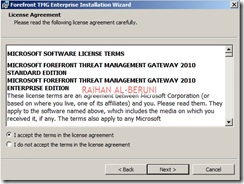
On the Installation Type page, select Forefront TMG Management only.
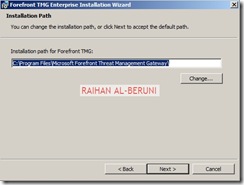
On the Installation Path page, you can change the default installation path.
On the Ready to Install the Program page, click Install.
After the installation is complete, if you want to open Forefront TMG Management select Launch Forefront TMG Management when the wizard closes.
Forefront TMG 2010 provide the following enhanced protection capabilities:
Understanding Network Topology
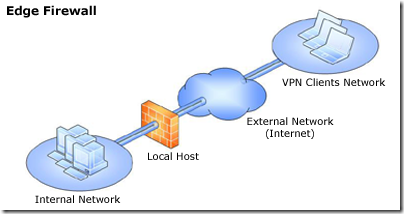
The following Forefront TMG network topologies are available:- Edge firewall—In this topology, Forefront TMG is located at the network edge, where it serves as the organization’s edge firewall, and is connected to two networks: the internal network and the external network (usually the Internet).

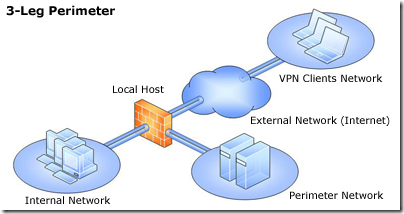
- 3-Leg perimeter—This topology implements a perimeter (DMZ) network. Forefront TMG is connected to at least three physical networks: the internal network, one or more perimeter networks and the external network.

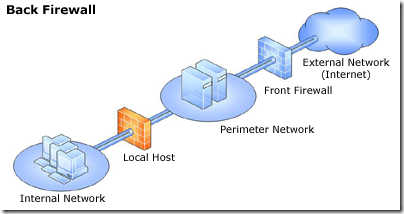
- Back firewall—In this topology, Forefront TMG is located at the network’s back-end. Use this topology when another network element, such as a perimeter network or an edge security device, is located between Forefront TMG and the external network. Forefront TMG is connected to the internal network and to the network element in front of it.


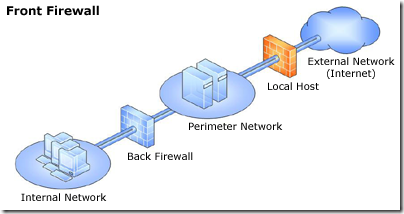
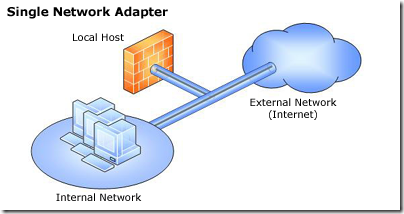
- Single network adapter—This topology enables limited Forefront TMG functionality. In this topology, Forefront TMG is connected to one network only, either the internal network or a perimeter network. Typically, you would use this configuration when Forefront TMG is located in the internal corporate network or in a perimeter network, and another firewall is located at the edge, protecting corporate resources from the Internet.

Functionality of a single network adapter topology
The single network adapter topology enables limited Forefront TMG functionality, that includes:- Forward (CERN) proxy for HTTP, HTTPS, and CERN proxy FTP (download only).
- Web caching for HTTP and CERN proxy FTP.
- Web publishing. HTTP-based communications, such as Microsoft Office SharePoint Server, Exchange Outlook Web Access 2007, ActiveSync®, and remote procedure call (RPC) over HTTP (Outlook Anywhere, Terminal Services Gateway or WSMAN-based traffic).
- Dial-in client virtual private network (VPN) access.
Limitations of a single network adapter topology
The following limitations apply when you use the single network adapter topology:- Server publishing and site-to-site VPN are not supported.
- SecureNAT and Forefront TMG Client traffic are not supported.
- Access rules must be configured with source addresses that use only internal IP addresses.
- Firewall policies must not refer to the external network.
Hardware Requirements
Systems requirements depends on number of users and deployment scenario. Forefront TMG is a vital part in a ICT infrastructure. To achieve best performance, you must add best processing power and memory in TMG server however the following will give you an optimum performance.Processor- Intel Xeon (Dual core/Quad-core/i7) or AMD Opteron (dual core/quad core). Intel Hyper-Threading Technology enabled in bios if Intel server board.
RAM-8GB
Disk Space –50GB systems partitions and 150GB logging +60GB-100GB Web caching in a separate partition. RAID 5 config would be highly recommended.
NIC- 2 Gigabit NIC with redundant config (number of NICs depends on deployment scenario)
Important! Forefront TMG has been built on 64 architecture.
Operating Systems and features
Windows Server 2008 SP2 64 bit or Windows Server 2008 R2Microsoft .NET Framework 3.5 SP1
Windows Web Services API
Network Policy Server.
Routing and Remote Access Services.
Active Directory Lightweight Directory Services Tools.
Network Load Balancing Tools.
Windows Power Shell
Windows Installer 4.5
Important! It’s not recommended to install any application or programme in TMG server other then antivirus program. It must be a dedicated server for Forefront TMG. Disable unnecessary services after installing operating systems. Install Machine Certificate from Enterprise Root CA Authority before installing TMG. TMG server must be a member of Active Directory Domain.
Installation of Forefront TMG
Prepare a 64 bit Windows Server 2008. Insert Forefront TMG DVD into the server. Run preparation tools.
Click continue on UAC authorization prompt.







Check Launch TMG installation. Click finish.







Add ranges of internal IP address For example: 10.10.10.1 to 10.10.10.255. You can as many subnet ranges as you have for internal networks.









Open Forefront TMG Management from start menu. TMG will automatically prompt you for initial configuration.

Step1: Network Setup Wizard—Use to configure network adapters on the server. Network adapters are associated with a unique Forefront TMG network. Note that you must have static IP address in all NIC of TMG server before you proceed for network settings.


This is highly important part of config because in this section you will mention what type of network topology you are going to use. Here, I am configuring De-militarized Zone (DMZ) or 3-Leg Perimeter. You have to select your desired config.




In this section, you have to select the behaviour of the traffic among internal, perimeter (DMZ) and external network. For example, My Forefront TMG 2010 server has been configured to route between internal and perimeter and NAT in between perimeter and external as I choose private networks in perimeter. So that I can hide IP addresses of my perimeter networks.


Step2: System Configuration Wizard—Use to configure operating system settings, such as computer name information and domain or workgroup settings




Step3: Deployment Wizard—Use to configure malware protection for Web traffic, and to join the customer feedback program and telemetry service.









Networks, Proxy and Update Configuration
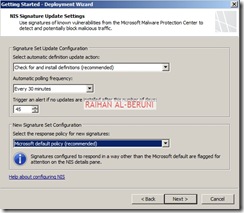
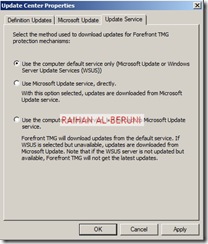
Open Forefront TMG Management. On the left hand pan, Select Update Centre. Click configure settings on task pan. Set update policy. If you have Windows Server Update Services (WSUS) then you may select WSUS or use Microsoft update services.
Select networking>Select Networks Tab>Double click on Internal. You will be presented with Internal Properties. Configure all the tabs as shown below.


In the domain tab, add internal domain(s). For example: *.wolverine.com.au


In the web browser tab, check Bypass Proxy… and Directly Access….

Verify all your internal IP addresses you added during installation. In this window you can add more internal IP addresses if you want.

Check Publish Automatic Discovery information for the network and use port 80 as default.

In Forefront TMG Client settings, Check Enable Forefront TMG client support for this network. un-check Automatically detect settings and Use automatic scripts.., Check Use a Web proxy server

In the Web Proxy Tab, Enable HTTP and use port 80 as default. However, you can use port 8080 if you want. Click on authentication and check integrated. Click on advanced and check unlimited. Now Apply and ok.


Apply changes.


Now repeat all these config for perimeter networks as you did for internal networks.
Connecting Active Directory, DNS and DHCP
Setup connectivity with Microsoft Active Directory, DNS and DHCP. Click on monitoring>click connectivity verifiers>Click Create New Connectivity Verifier. Create connectivity for Active Directory, DNS and DHCP.



Click Next and Finish. Repeat it for DNS and DHCP. If you have a upstream Proxy, connect to upstream proxy using similar method.
Create HTTP and HTTPS rule
By default all access rules are denied. Now Create web access rules for internal networks allowing HTTP and HTTPs traffic pass through from internal network to external and perimeter. Also allow HTTP and HTTPs traffic pass through from perimeter to external and internal. Click Firewall Policy>Click Create Access Rule on Task Pan.












Test Forefront TMG Setup
Now moment of truth. Log on to a computer using domain user credential in any internal network. Setup proxy in IE connections and browse internet.



This comment has been removed by the author.
ReplyDeleteIts Nice
ReplyDelete