Since Apple first released the iPhone, it has gained significant
market share in the mobile phone market world-wide. The phone uses 3G
and 4G data services in addition to WiFi connection(s). This allows it
to be used as a comprehensive communications device from anywhere data
services are available. One of the iPhone's most popular features is
allowing users to set custom ringtones for individual callers, SMS
text messages, new email, and alarm settings. A common task that iPhone
users face is making new ringtones from popular songs or other audio
sources.
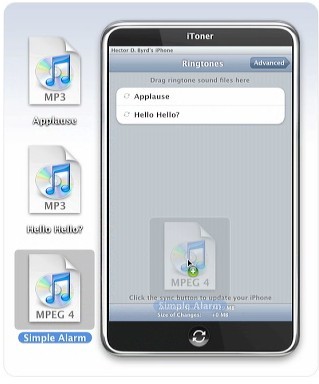
Step 2 – Pick a song from your iTunes library.
Step 3 – Pick a part of the song that you want to use for the ringtone. iTunes and the iPhone will only support a ringtone that is up to 35 seconds in duration. Note the starting and stopping point on the iTunes player for the part of the song that you want to make into a ringtone.
Step 3 – Right click the song title (Ctrl Click on the Mac).
Step 4 – Select “Get Info” then enter the starting and stopping times for the ringtone selected from Step 3.
Step 5 – Choose the “Advanced” and “Create AAC” menu options to create an AAC from the existing song in your iTunes library. If this option is not available, click “Edit,” “Preferences,” and “General” and change the import settings to “AAC” as the preferred format.
Step 6 – Ctrl Click (on a Mac) or right click the new AAC file and choose “Show in Explorer.” Rename the file with a new file extension, “.m4r”
Step 7 – Delete the AAC file created from the iTunes library and then drag the .m4r file onto the iTunes desktop to load the new ringtone into your library.
Step 8 – Move the ringtone file from your iTunes library to your phone by dragging the song icon onto the iPhone icon in iTunes to complete loading the new ringtone. * Note that your phone must be connected to the computer for it to appear in the iTunes menu.
How to Make Ringtones for the iPhone
Step 1 – Open the iTunes program on the computer. The application is installed in the Mac computer doc by default and will install a program icon on the Windows computer's desktop.
Step 2 – Pick a song from your iTunes library.
Step 3 – Pick a part of the song that you want to use for the ringtone. iTunes and the iPhone will only support a ringtone that is up to 35 seconds in duration. Note the starting and stopping point on the iTunes player for the part of the song that you want to make into a ringtone.
Step 3 – Right click the song title (Ctrl Click on the Mac).
Step 4 – Select “Get Info” then enter the starting and stopping times for the ringtone selected from Step 3.
Step 5 – Choose the “Advanced” and “Create AAC” menu options to create an AAC from the existing song in your iTunes library. If this option is not available, click “Edit,” “Preferences,” and “General” and change the import settings to “AAC” as the preferred format.
Step 6 – Ctrl Click (on a Mac) or right click the new AAC file and choose “Show in Explorer.” Rename the file with a new file extension, “.m4r”
Step 7 – Delete the AAC file created from the iTunes library and then drag the .m4r file onto the iTunes desktop to load the new ringtone into your library.
Step 8 – Move the ringtone file from your iTunes library to your phone by dragging the song icon onto the iPhone icon in iTunes to complete loading the new ringtone. * Note that your phone must be connected to the computer for it to appear in the iTunes menu.












